According to our telemetry, the Milum Trojan was exclusively used to attack targets in the Middle East from at least the end of May 2019.
Link: https://securelist.com/wildpressure-targets-industrial-in-the-middle-east/96360/
Summary:
- Authored by Denis Legezo and posted on securelist.com on 24th March 2020, the article summarises the technical elements of this recently observed campaign by Kapsersky
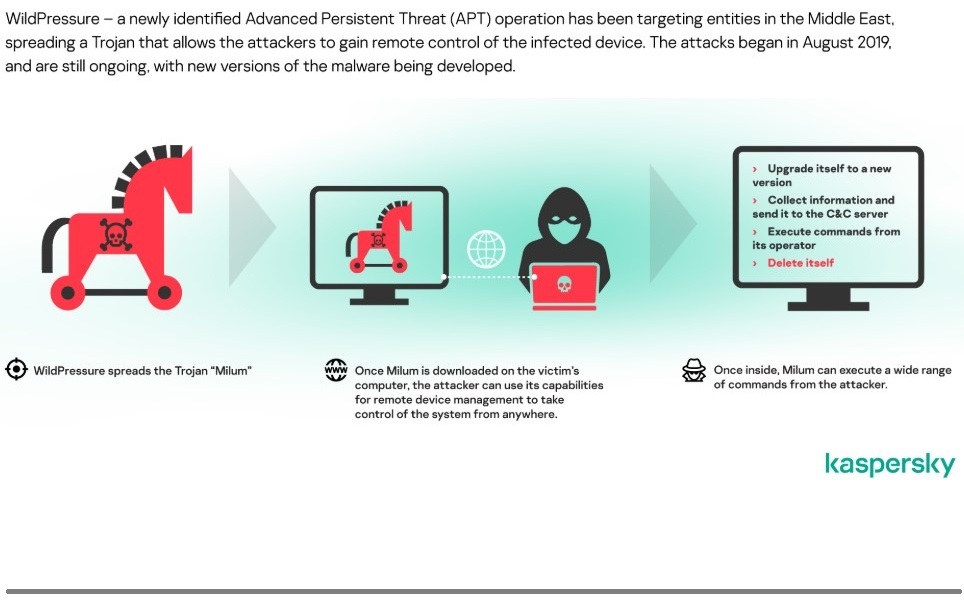
- Kaspersky first detected the new C++ Trojan in May 2019 hitting companies in the Middle East, many in industrial sector
- Based on various field samples the samples seem unique implying the attacks are targeted
- Kaspersky sinkholed the a C2 domain and monitored traffic, almost all of which was from Middle East
- Kaspersky dubbed the campaign WildPressure, and named the trojan Milum
- Kaspersky products initially detect this malware as Backdoor.Win32.Agent
- WildPressure is an ongoing operation to this day
- New versions of Milum being developed and spread
- Trojans are hidden in PE files of the exe Milum46_Win32.exe or system32.exe
- The malware allows remote control of infected devices
- The code doesn’t appear deceptive on the surface – e.g, compilation timestamp is consistent with samples first-seen time, C2 HTTP header info shows early code versioning and plans for non C++ versions
- The most prolific sample detected is an application that exists as an invisible toolbar window
- So far not able to attribute the campaign to a threat actor or group
- The C++ code, config, and comms are relatively generic
- The trend of copy-catting interesting threat actors and use of common code means attribution requires stronger correlations
- So far the spreading mechanism isn’t known
- Kaspersky also speculates that the true targets aren’t known. The observed ‘victims’ to-date are possibly stepping-stones to other companies
Extracted IOCs and Artefacts:
Files MD5:
- 0C5B15D89FDA9BAF446B286C6F97F535
- 17B1A05FC367E52AADA7BDE07714666B
- A76991F15D6B4F43FBA419ECA1A8E741
- Original file names are Milum46_Win32.exe; on the target side they exist as system32.exe
URLs:
- upiserversys1212[.]com/rl.php
- 37.59.87[.]172/page/view.php
- 80.255.3[.]86/page/view.php
Share Post:




