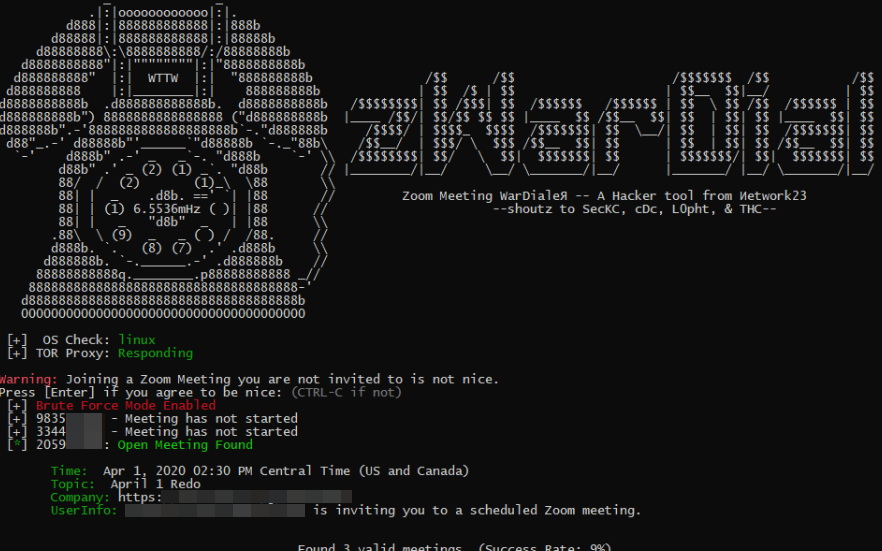
“Each Zoom conference call is assigned a Meeting ID that consists of 9 to 11 digits. Naturally, hackers have figured out they can simply guess or automate the guessing of random IDs within that space of digits.“
Link: https://krebsonsecurity.com/2020/04/war-dialing-tool-exposes-zooms-password-problems/
Summary:
- Authored on April 2nd by Brian Krebs at Krebsonsecurity.com, the article details the most recent of many of Zoom‘s security issues
- Last year hackers figured out they can automate the guessing of random Meeing IDs, allowing them to join any of those Meetings, dubbed as “Zoombombing“
- Zoom said last year that they fixed the issue by:
- enabling passwords by default in all future scheduled meetings;
- blocking repeated attempts to scan for meeting IDs;
- no longer automatically indicating if a meeting ID was valid or invalid
- Newly discovered tool known as zWarDial evades Zoom’s attempts to block automated meeting scans by routing the searches through multiple proxies in Tor
- zWarDial found Nearly 2,400 upcoming or recurring Zoom meetings in a day. Validated info includes:
- The link needed to join each meeting;
- The date and time of the meeting;
- The name of the meeting organizer;
- and any information supplied by the meeting organizer about the topic of the meeting
- Zoom meetings discovered by some of the worlds largest companies
- By far the largest group of companies exposing their Zoom meetings are in the technology sector
- “Having a password enabled on the meeting is the only thing that defeats it,”
- Zoom has acknowledged the issue and is investigating the technicalities.
- They’re also investigating the possibility that its password-by-default approach may fail under certain circumstances
- Zoom states: “Passwords for new meetings have been enabled by default since late last year, unless account owners or admins opted out,”
- The statement continues “We are looking into unique edge cases to determine whether, under certain circumstances, users unaffiliated with an account owner or administrator may not have had passwords switched on by default at the time that change was made.”
Share Post:




