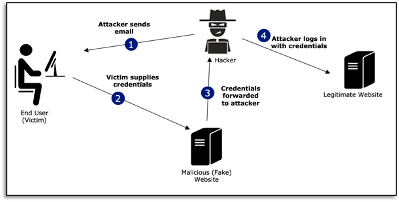
• Implementing the DMARC protocol to authenticate emails and prevent phishing attacks.
• Verifying the authenticity of email senders by checking for domain matches in the “From” header.
• Ensuring that MX records are pointing to legitimate mail servers.
• Scanning for malicious activity with Urlscan.io and screenshotmachine.com.
• Utilizing a sandbox for static analysis to identify malicious file attachments.
• Educating personnel on how to spot phishing techniques.
• Utilizing multi-factor authentication.
• Enforcing regular security assessments.
Share Post:




