” The fact that dark_nexus is built on the foundations of Mirai and Qbot is proof of the evolving tactics of botnet operators and inexperienced hackers alike…”
Link:
Summary:
- Authored by Ravie Lakshmanan on 8th April 2020 at Hackernews.com, the article details a new variant of IOT Botnet Malware dubbed Dark Nexus by BitDefender security researchers
- Primary infection mechanism is credential stuffing on targeted IOC devices such as routers, video recorders, and thermal cameras
- Once infected the goal of Dark Nexus is to co-opt the device in to a botnet
- Nearly 1,500 devices in the botnet at the time of writing, and growing
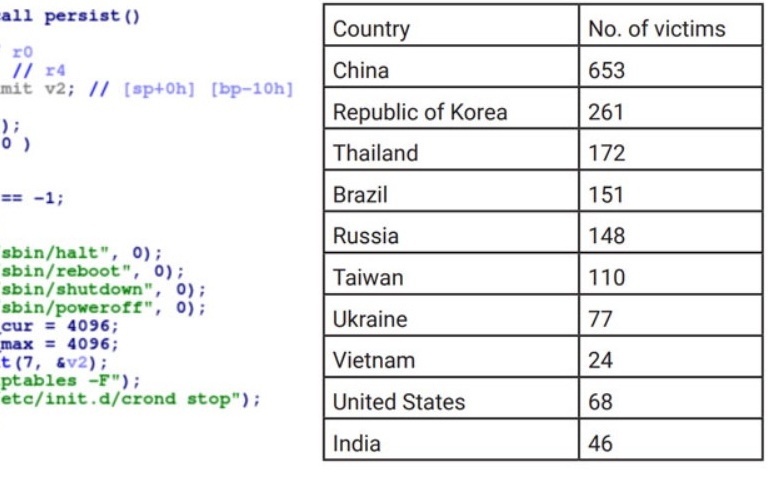
- Bots observed in China, South Korea, Thailand, Brazil, and Russia
- The botnet acts as reverse proxy
- Dark Nexus is in constant development with nearly 30 versions released in last 4 months
- Evidence gathered by Bitdefender points to greek.Helios as the individual behind the development
- Some modules of the malware resemble known variants such as Qbot & Mirai
- Startup code resembles Qbot – Forks several times, blocks several signals, and detaches itself from the terminal
- Similar to Mirai, it binds to a fixed port (7630), changes its name to ‘/bin/busybox‘, and disables ioctl calls on the device
- However it’s more potently unique in other ways:
- Payloads compiled for 12 different CPU architectures, dynamically delivered based on the victim config
- Uses a unique scoring system based on weights and thresholds to assess risky processes and subsequently removes them
- Disables Cron Service and removes privileges to prevent reboot
- Relatively straight-forward C2 registration:
- C2 Servers at switchnets[.]net:30047 and thiccnigga[.]me:30047 issue remote commands and manage initial infection
- Once brute-force succeeds, the bot registers to switchnets[.]net:80, identies CPU architecture & transmits custom infection payload via Telnet
- Full technical write-up can be downloaded as a Whitepaper from Bitdefender: https://www.bitdefender.com/files/News/CaseStudies/study/319/Bitdefender-PR-Whitepaper-DarkNexus-creat4349-en-EN-interactive.pdf
Extracted Indicators (abbreviated):
- Port: 7630
- Port: 30047
- Entity Name: ‘/bin/busybox’
- Process: ioctl calls
- Process: Cron Service
- Server: switchnets[.]net:30047
- Server: thiccnigga[.]me:30047
- Server: switchnets[.]net:80
- Threat Actor: greek.Helios
Share Post:




