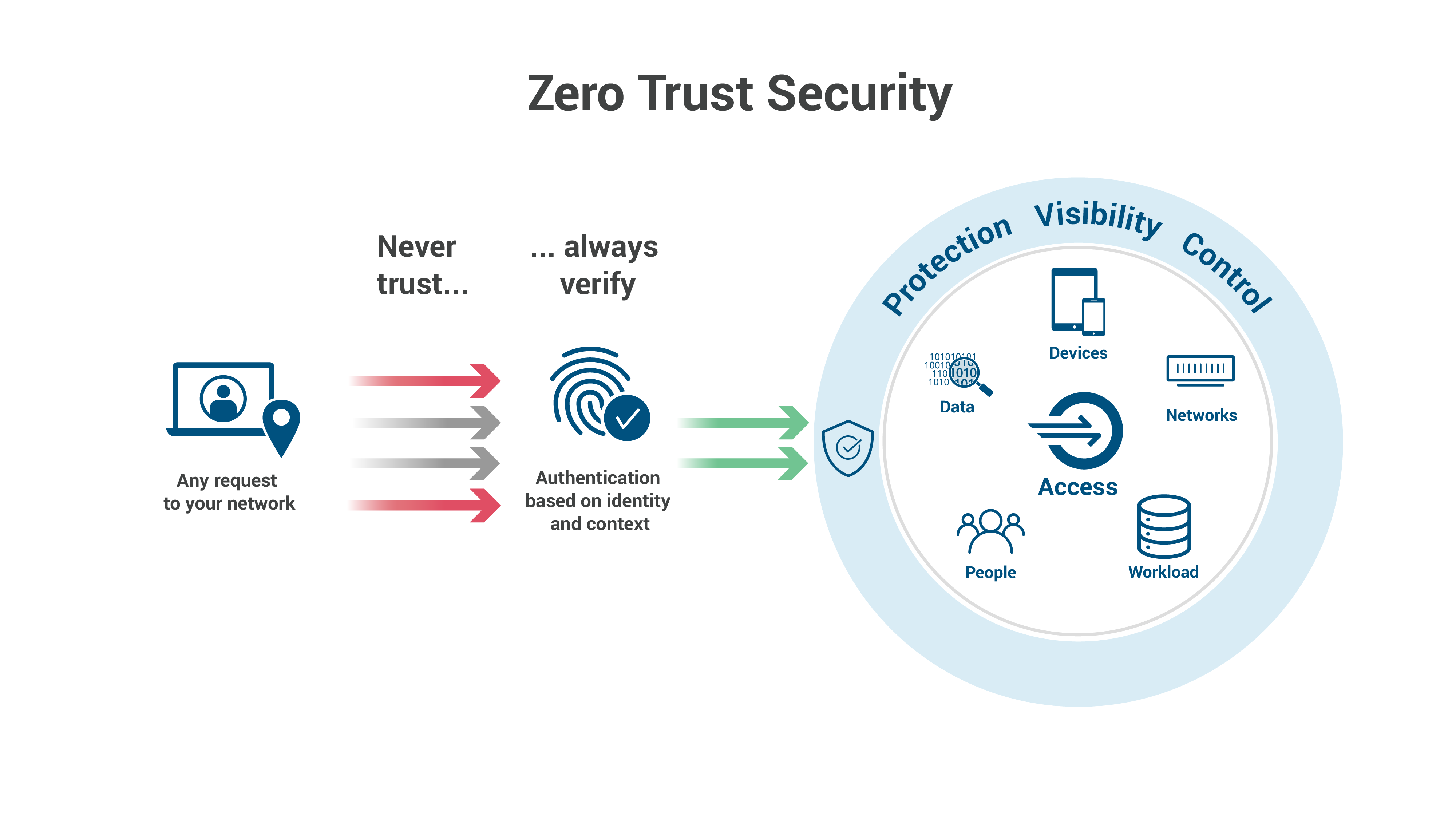
Source: https://www.blackfog.com/what-you-need-to-know-about-zero-trust-identity-and-access-management/
-Organizations with many users connecting to public cloud infrastructure from outside the network perimeter can be vulnerable to data breaches.
-VPNs can be used to protect against cyber threats, but may be cumbersome and inefficient.
-Individuals from outside the organization, such as contractors and suppliers, have access to the main site which can bypass location-based access management tools.
-System admins, software developers, and DevOps professionals with higher levels of access must be closely monitored.
-Internet of Things (IoT) devices can collect sensitive data, yet they are not secure by default.
-A zero trust policy should be implemented to minimize the risk of data leaks.




